Simplifying Security Compliance with Managed Identity
What is Azure Managed Identity?
Azure Managed Identity is a service that provides Azure resources with automatically managed credentials for authentication to other Azure services that support Azure AD authentication. This eliminates the need to store or manage secrets directly in your applications.
Essentially, it acts as a digital identity for your applications, granting them access to various Azure services without requiring explicit credentials.
Types of Managed Identity
There are two primary types of managed identity in Azure:
- System-assigned Managed Identity: This is automatically created and managed by Azure when you enable it for a resource. It's associated exclusively with that specific resource.
- User-assigned Managed Identity: This is a standalone resource that can be assigned to multiple Azure resources. It offers greater flexibility and control over access management.
Benefits Azure Managed Identity?
- Enhanced Security: By removing the need to store and manage secrets within your application, you reduce the risk of unauthorized access.
- Simplified Development: Managed Identity simplifies the authentication process, allowing you to focus on building your application's core functionality.
- Improved Compliance: Managed Identity aligns with security best practices and can help you meet compliance requirements.
How Does it Work?
- Assignment: You assign a managed identity to an Azure resource.
- Authentication: When the resource needs to access another Azure resource, it presents its managed identity for authentication.
- Authorization: Azure Active Directory (Azure AD) evaluates the permissions granted to the managed identity and authorizes or denies access.
Common Use Cases
- Azure Functions: Authenticating Azure Functions to access other Azure resources like storage accounts, databases, or key vaults.
- Azure App Services: Granting access to Azure services like Azure SQL Database or Azure Cosmos DB.
- Virtual Machines: Enabling secure communication between virtual machines and other Azure resources.
- Azure Logic Apps: Authenticating Logic Apps to interact with various Azure services and external systems.
Example Case Study
Let's walk through a practical example of using Managed Identity to access an Azure Key Vault.
Prerequisites:
Below are the resources that we are going to work with to demonstrate this example.
- An Azure subscription
- An Azure Key Vault
- An Azure App Service (or other Azure resource that supports Managed Identity)
Steps:
-
Create an Azure Key Vault:
- Go to the Azure portal and search for "Key Vault".
- Click "Create" and follow the instructions on the portal to create a new Key Vault. (Complete steps are mentioned here.)
-
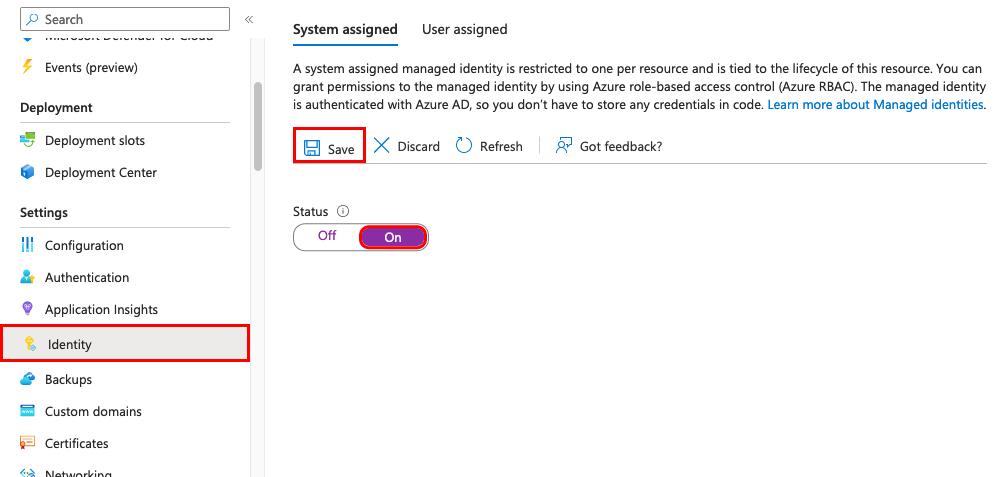
Enable Managed Identity on Azure WebApp:
- Go to the webapp's settings pane.
- Under "Identity", select "System-assigned".
- Save the changes.
-
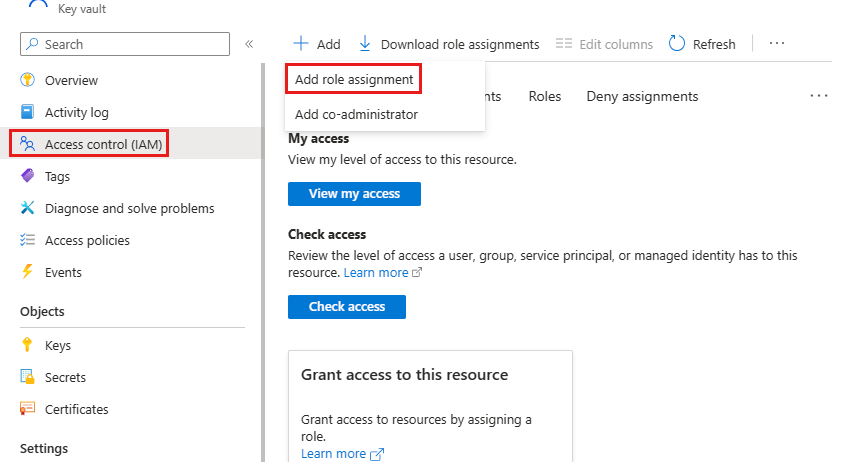
Grant Access to the Key Vault:
-
Go to your Key Vault's access policies.
-
Click "Add".
-
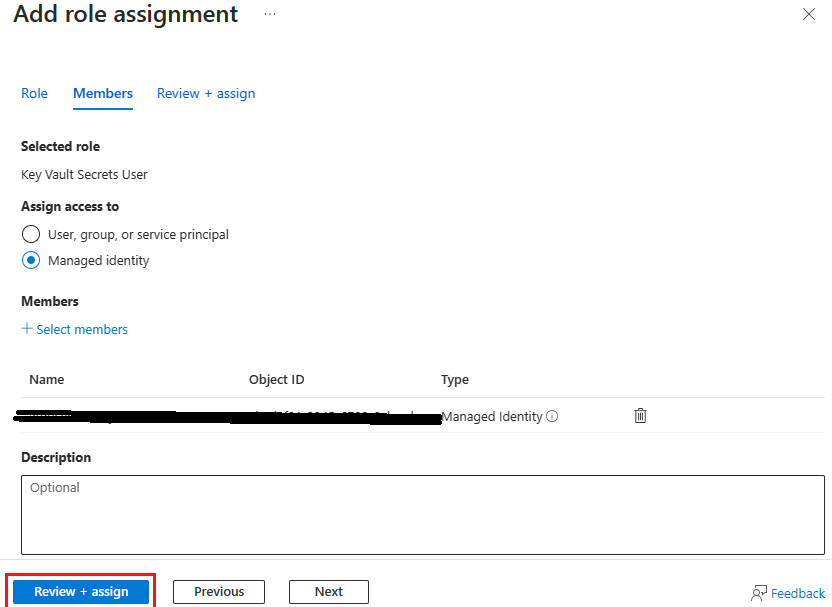
Select "Add Role Assignment".
-
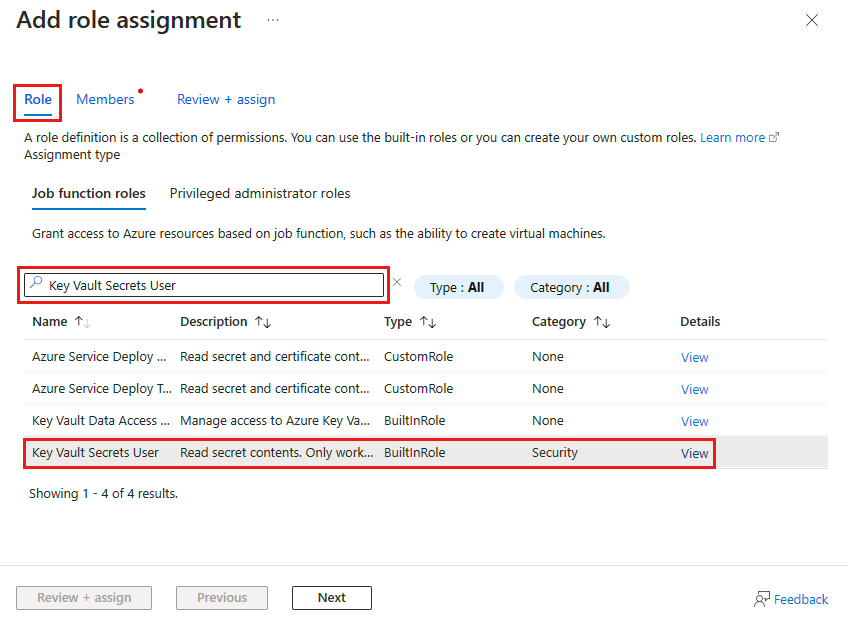
Choose the appropriate permissions (e.g., "Key Vault Secrets User").
-
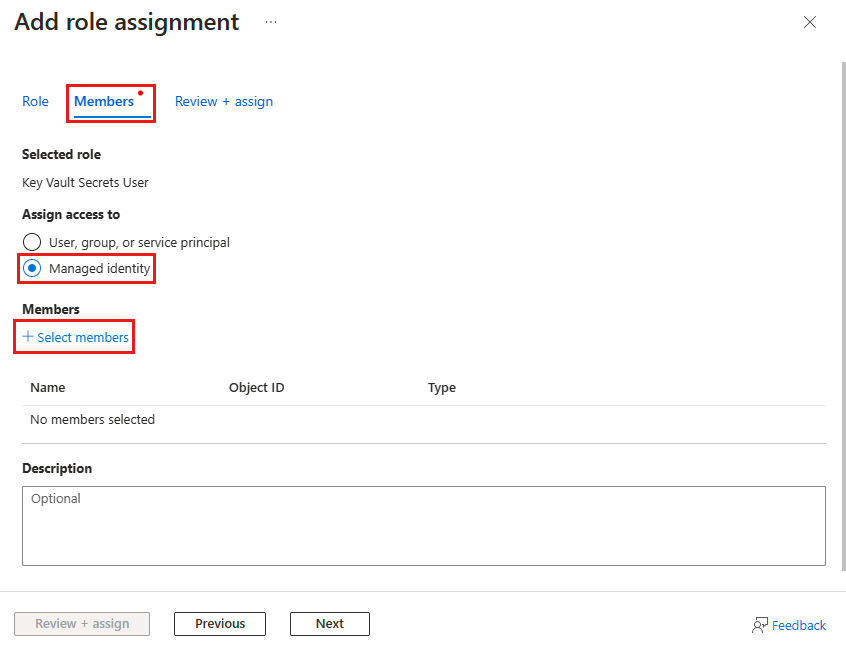
For "Assignment", select "Managed Identity".
-
Search for the system-assigned managed identity of your webapp and select it.
-
Save the changes.
-
-
Access the Key Vault from Your Application:
- In your application's code, use the appropriate Azure SDK to authenticate using Managed Identity. For example, in C#, you can use the
Azure.Identitylibrary:
using Azure.Identity; using Azure.Security.KeyVault.Secrets; // ... var credential = new DefaultAzureCredential(); var keyVaultClient = new SecretClient(new Uri("https://your-key-vault-name.vault.azure.net/"), credential); var secret = keyVaultClient.GetSecret("your-secret-name"); Console.WriteLine(secret.Value); - In your application's code, use the appropriate Azure SDK to authenticate using Managed Identity. For example, in C#, you can use the
Another Case Study Reference: Access Secrets from Azure Key Vault for Azure Frontdoor